Updated July 2025: Stop error messages and fix your computer problem with this tool. Get it now at this link
The input personalization app runs in the background while you are typing on your computer. You don’t even notice it.
When you type out a document, the handwriting recognition software converts your handwritten letters into words automatically.
You can use the app to train your device’s handwriting recognition software. After training, you can start typing without having to manually select each letter.
This tool helps you to write down notes and memos faster.
Overview
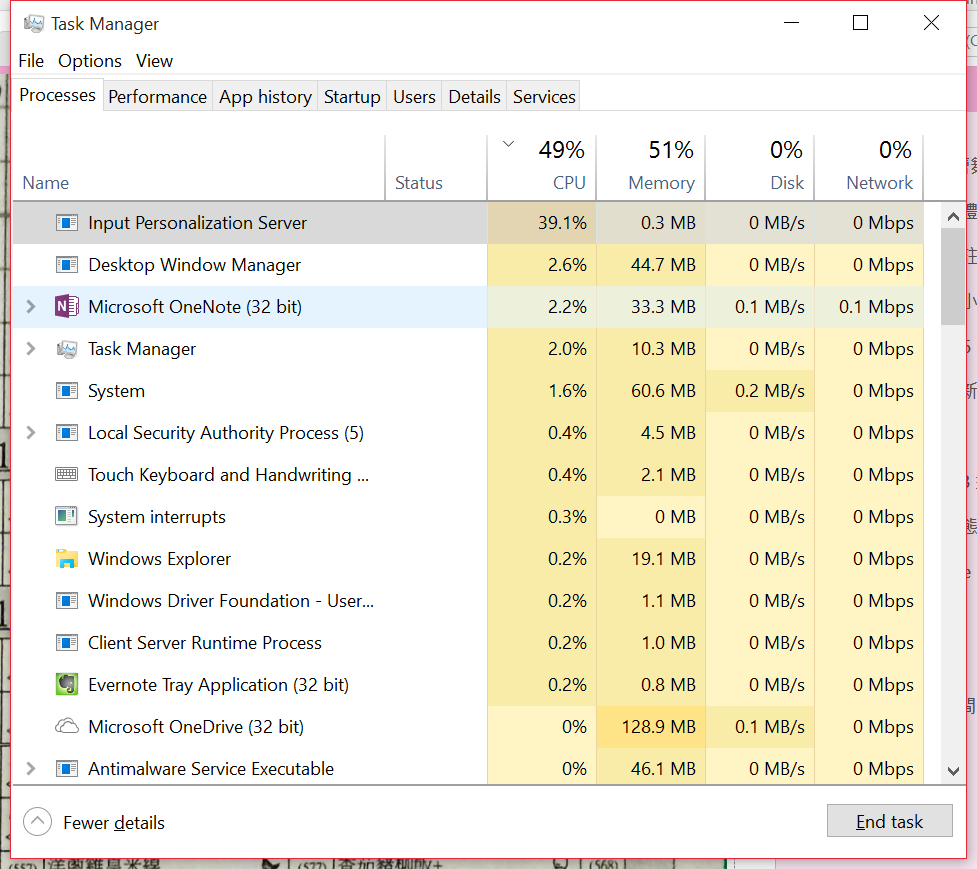
inputpersonalization.exe is a Microsoft Windows application that runs on x86 based systems. This tool is used to configure the system settings and provides information about the current state of the computer hardware and software.
The file size of inputpersonalization.exe is 566.72 KB (569,848 bytes).
inputpersonalization.exefeatures the following main executable modules:
* inputpersonalization.exe
* inputpersonalization_x64.exe
* inputPersonalization.msi
* inputpersonalizationui.dll
What is inputpersonalization.exe?
InputPersonalizationServer.exe is a handwriting recognition software application developed by Microsoft Corporation. This site allows you to use your Tablet PC to write notes, messages, emails, etc., and the program will convert it into text.
You can download InputPersonalizationServer.exe directly from Microsoft’s Website.
Programs installed in
This utility installs the following subprograms:
* Accessibility Utilities
* Voice Recognition Utility
* Touchscreen Utilities
* Universal Serial Bus Utilities
We highly recommend that you use this tool for your error. Furthermore, this tool detects and removes common computer errors, protects you from loss of files, malware, and hardware failures, and optimizes your device for maximum performance. This software will help you fix your PC problems and prevent others from happening again:
Updated: July 2025
How to disable Inputpersonalization.exe
Please read this critical warning first: A general tutorial on how to delete any file from your computer is provided in this post. That inputpersonalization.exe is dangerous is NOT implied at all! Be cautious when deleting executable files from your computer without first performing some research. First off, since inputpersonalization.exe is an executable, there is always a chance that deleting it could harm your data or the operating system.
- Create a Windows restore point (not available in Windows XP). In the event that something goes wrong, the restore point will allow you to undo modifications.
To open the regular search window. - press the F3 key. Enter “inputpersonalization.exe” into the search box after that. If you’re lucky, Windows will locate all the copies in a matter of minutes.
- Try to find the application that inputpersonalization.exe is a part of. then attempt to remove that software using a regular method.
For instance, inputpersonalization.exe is most likely a part of the “Dummy game” software package if it is located in the location C:Program FilesDummy game**some subfolder**. - If the issue still exists and you are unable to remove the file in this manner, go to the search results in step 2 and attempt to manually remove every instance of inputpersonalization.exe there.
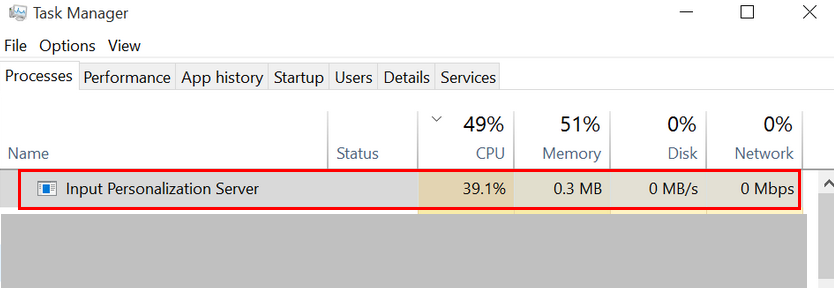
Note: You won’t be able to remove the file if the process is already active. In this case, you must use Task Management to terminate the process (right-click the Windows task bar and choose “Task manager”). - Click the “Processes” pane in the Task Manager panels. the “Delete” key after selecting inputpersonalization.exe). detailed manual
Maintain regular computer maintenance. Abandoned files and other “computer garbage” are completely automatically cleaned up by specialized applications like IT Sponge.
Behaviors
InputPersonalization.exe runs scheduled tasks on logon, bypasses User Account Control (UAC), and allows local administrators to use the program without elevation.
The following are some of the ways that InputPersonalization.exe behaves differently depending on whether it is running under normal conditions or elevated.
1. When running normally, InputPersonalization.exe does not prompt for administrative privileges. Instead, it runs with standard user permissions. This behavior is expected because the application runs with the same security context as the logged-in user.
2. When running under elevated privilege, InputPersonalization.exefails to display the “Run As Administrator” dialog box.
3. When running under elevated privileges, InputPersonalization.Exeis able to modify registry settings and files outside of Program Files.
4. When running under elevated priviliges, InputPersonalization.EXEallows the creation of shortcuts on the desktop even though the application is not installed there.
5. When running under elevated privilegies, InputPersonalization.XEallows the creation of shortcut icons on the Start menu even though the application is uninstalled.
All file variations of inputpersonalization.exe
Malware authors often use multiple versions of the same malicious program. They do this because it makes it harder to detect and stop infection. If you download one version of the malware, but another version gets into your system, you won’t know about it. You’ll just think everything is fine.
The most common way malware spreads is through files. Malicious programs usually come packaged in some form of installer. These installers include.EXE,.MSI,.ZIP, and others. When you download such a file, it might look like a legitimate application you want to install. However, once installed, the program could start automatically every time you boot up your computer. Or it could silently steal information from your system.
This video demonstrates how malware uses file variations to spread itself across your PC.
Distribution by PC manufacturer
Amazon dominates the ecommerce space, accounting for nearly half of total retail sales worldwide. But it isn’t just about selling products; it’s about making sure those products reach consumers. To do that, Amazon relies on distribution partners like Ingram Micro, which helps the retailer fulfill customer orders. In fact, Amazon uses Ingram Micro’s technology to track inventory across multiple warehouses and even different countries.
But while Amazon is known for being one of the largest sellers of consumer electronics, it doesn’t dominate the entire industry. For example, Apple sells more iPhones than anyone else, but Samsung makes more smartphones overall. And according to data compiled by research firm Gartner, Dell ranks third among global computer makers behind HP and Lenovo.
In some regions, however, Dell does lead the pack. For instance, in China, Dell is the leading PC vendor, followed closely by Lenovo. In India, Lenovo leads the way, followed by Dell and Hewlett Packard Enterprise. In Latin America, Dell is the leader, followed by Acer and Lenovo.
As you might imagine, each of these companies has a unique story to tell. We took a look at how Dell compares to its competitors based on data from Gartner, IDC, Statista, and our own analysis.
RECOMMENATION: Click here for help with Windows errors.
Frequently Asked Questions
Is SettingSyncHost.exe a virus?
The malicious software named SettingSyncHost.exe is being used to steal data from computers running Windows 7 and 8 operating systems. This malicious program is disguised as a legitimate process called SettingSyncHost.exe. It appears in the list of processes running on the computer. But it does not seem to do anything useful. However, it looks like there are some people out there who want to use it for something else.
Usually, cybercriminals set names of viruses in such ways that the system or the end user cannot identify them. They might even change the extension, making it look different from the original virus. In this case, the malicious software is called SettingSyncHost.exefor example. So, what makes this one special? Well, the name of the file itself is misleading; it actually does nothing.
SettingSyncHost.exe is located in the System 32 folder. Right-clicking on the process in the task manager and selecting open file location opens another window where you can see the path to the executable.
If the place is any other folder than the System32 folder then run a full system antivirus scan on the system and delete the malicious files.
How to Stop Windows from Posting Errors
If none of the methods above seem to fix your Werfaulterrors, you can try turning off the Windows Error Reporting Service entirely. To do so, follow these easy instructions:
Pressand holdtheWindowskeyon your keyboard,then hit R.
This shortcut launches the Run utility.
Typeservicess.mscin theinputfield, then click the OK button.
You’ll now see a list of services, including the Windows Error Reporting Service.
Click the Disabledcheckbox next to theservice name, then click the OKbutton.
That’s it; your error reports won’t be sent anymore.